The Importance of Multi-Factor Authentication (MFA)
MFA: Unlocking the Importance Benefits of Multi-Factor Authentication
In today’s increasingly interconnected and threat-laden digital landscape, ensuring robust cybersecurity is paramount. One of the most effective and readily deployable defenses against unauthorized access and data breaches is multi-factor authentication. MFA significantly enhances security by requiring users to provide multiple authentication factors to verify their identity, creating a formidable barrier against cyber threats. This article explores the intricacies of MFA, its mechanisms, various authentication methods, and the myriad benefits it offers to individuals and organizations alike.
Understanding MFA
What is Multi-Factor Authentication?
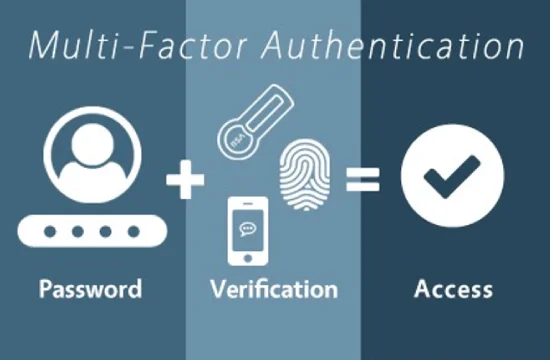
Multi-factor authentication is a security measure that demands users present multiple authentication factors to gain access to a system or application. Unlike traditional, one-factor authentication that relies solely on a password, MFA requires users to verify their identity through at least two different authentication methods. This additional layer of security makes it significantly more difficult for cyber attackers to gain unauthorized access, even if they have compromised a user’s password. The core principle of multi-factor authentication is to bolster the security of user authentication by leveraging independent credentials.
How MFA Works
The authentication process in an MFA system involves verifying a user’s identity through multiple authentication factors drawn from different categories. These categories typically include something you know (a password or security question), something you have (a security token, authenticator app on your smartphone), and something you are (biometric authentication like fingerprint or facial recognition). When a user attempts to log in, the system prompts them for their primary credential, usually a password. Upon successful verification of the password, the MFA system then requests an additional authentication factor, such as a code generated by an authenticator app or a biometric scan.
Types of MFA Authentication Methods
Various multi-factor authentication methods are available, each offering a unique approach to enhancing security. Some of these methods can be summarized as follows:
| Authentication Factor | Examples |
|---|---|
| Possession Factor | Security token, Microsoft Authenticator, Google Authenticator |
| Knowledge Factor | Password, answers to security questions |
Biometric authentication methods leverage unique biological traits, like fingerprint scanning or facial recognition, as factors of authentication in strong authentication systems. Adaptive MFA, also known as risk-based authentication, dynamically adjusts the level of security based on the risk associated with the access attempt.
Benefits of Multi-Factor Authentication
10 Benefits of Multi-Factor Authentication
The benefits of multi-factor authentication are extensive, providing a robust defense against a wide array of cyber threats. By requiring users to verify their identity through multiple authentication factors, such as something they know, something they have, or something they are, MFA significantly reduces the risk of unauthorized access. A compromised password alone is no longer sufficient for an attacker to gain entry, as they would also need to bypass the additional authentication. This added layer of security effectively thwarts many common attack vectors, including phishing, password reuse, and brute-force attacks, thus safeguarding sensitive data and systems. TeamWin is dedicated to ensuring the highest level of data security, making the implementation of MFA a cornerstone of our cybersecurity strategy.
Enhancing Cybersecurity with MFA
MFA significantly enhances cybersecurity posture by adding an extra layer of security that extends beyond traditional password-only systems. While passwords remain a crucial element of user authentication, their vulnerability to compromise necessitates the use of MFA to fortify access controls through strong authentication. MFA adds an extra layer of security, preventing unauthorized access even if a password is stolen or guessed, which is why strong authentication is essential. TeamWin’s comprehensive suite of IT security solutions includes robust MFA solutions tailored to meet the unique needs of our clients. These solutions are designed to be reliable and efficient, providing proactive threat management through vigilant monitoring and swift response strategies, ultimately safeguarding enterprise data and intellectual property.
Comparing MFA to Password-Only Security
The stark contrast between MFA and password-only security lies in their respective resilience against cyber threats. Password-only systems rely solely on a single authentication factor, making them highly susceptible to password-related attacks, which is why multifactor authentication is essential. In contrast, multi-factor authentication adds an extra layer of security by requiring at least two different authentication factors. This additional authentication drastically reduces the likelihood of a successful cyber attack, as even if a password is compromised, the attacker still needs to bypass the additional form of authentication. For example, use MFA with Microsoft Authenticator. TeamWin advocates for the implementation of MFA to significantly enhance security and protect against potential security breaches.
Implementing MFA
How to Use MFA Effectively
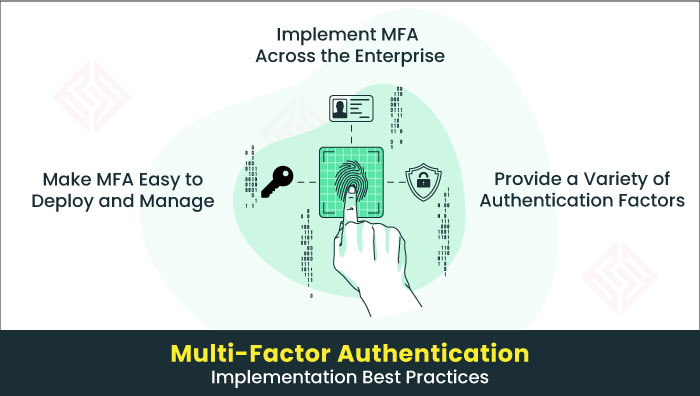
To effectively use MFA, organizations must start with a comprehensive understanding of their specific security needs and vulnerabilities. Consider factors like the sensitivity of the data being protected, the types of users accessing the system, and the potential risks involved in a multi-factor authentication system. Subsequently, implement MFA solutions that offer a variety of authentication methods to cater to diverse user preferences and security needs. User education is also paramount; ensure that users understand the importance of MFA and how to use it properly. For example, instruct users on setting up authenticator apps, using security keys, and recognizing phishing attempts. The authentication process should be seamless and not overly burdensome, striking a balance between security and usability in the multi-factor authentication work.
Choosing the Right MFA Solution
Selecting the appropriate MFA solution requires careful consideration of various factors to ensure it aligns with the organization’s unique requirements and risk profile. Teamwin Global Technologica emphasizes a custom-tailored approach to ensure the best fit and value for money for their clients. Begin by assessing the compatibility of the MFA solution with existing systems and applications. Evaluate its scalability to accommodate future growth and changing needs. Consider the range of supported authentication methods, prioritizing those that offer a high level of security and user convenience. They also prioritize educating their clients to help them choose the right solutions. Also, the solution should provide robust reporting and auditing capabilities to monitor its effectiveness and identify potential security gaps.
Common Authentication Methods in MFA
Here are several authentication methods commonly used in MFA, offering diverse approaches to bolster security. Two prevalent methods include:
- Using an authenticator app on a smartphone (like Microsoft Authenticator or Google Authenticator) that generates time-based one-time passwords (TOTP).
- Employing security keys, which are physical devices plugged into computers to verify identity.
Adaptive MFA, also known as risk-based authentication, dynamically adjusts the security level depending on the login attempt’s context.
Challenges and Considerations
Potential Drawbacks of MFA
While the benefits of multi-factor authentication are undeniable, potential drawbacks must be considered. One significant challenge is the inconvenience it may introduce for users. Requiring an additional authentication factor can slow down the login process, leading to frustration, especially if the authentication process isn’t seamless. Another consideration is the potential for lockouts if users lose access to their second factor, such as a phone. A poorly implemented MFA system can also create a false sense of security if the authentication methods are not robust. TeamWin emphasizes that the effective implementation of MFA includes addressing these potential drawbacks through careful planning and user education.
Addressing User Resistance to MFA
User resistance to MFA can be a significant hurdle to its successful adoption, highlighting the need for effective communication about the benefits of MFA. Many users may perceive the extra layer of authentication as an inconvenience, leading to pushback. To address this, it’s essential to communicate the importance of multi-factor authentication clearly, emphasizing how MFA ensures the protection of sensitive data and prevents security breaches. Simplify the authentication process by selecting user-friendly authentication methods like biometric authentication. Training and support are crucial to ensure users understand how to use the factors of authentication properly in a multi-factor authentication system. TeamWin is dedicated to providing comprehensive support to help organizations overcome user resistance and successfully implement MFA.
Future Trends in Multi-Factor Authentication
The future of multi-factor authentication is poised for innovation, driven by advancements in technology and the evolving threat landscape. One notable trend is the increasing adoption of biometric authentication, such as facial recognition and fingerprint scanning, which offer a convenient and secure authentication method. Adaptive MFA, or risk-based authentication, is also gaining traction, dynamically adjusting the level of security based on the risk associated with the access attempt. Integration of artificial intelligence (AI) and machine learning (ML) can further enhance MFA systems by analyzing user behavior to detect and prevent unauthorized access. TeamWin is dedicated to staying at the forefront of these emerging trends to provide our clients with the most advanced and effective MFA solutions.
5 Surprising Facts About the Importance of Multi-Factor Authentication (MFA)
- MFA can stop up to 99.9% of automated cyber attacks, significantly reducing the risk of unauthorized access.
- Many major data breaches occur due to compromised passwords; MFA adds an additional layer that is often overlooked.
- Research shows that organizations using MFA are 50% less likely to experience a data breach compared to those that do not.
- MFA is not just for large corporations; small businesses are increasingly targeted and can greatly benefit from implementing it.
- Adopting MFA can improve user trust and confidence, as customers feel more secure knowing their accounts have extra protection.
What is multi-factor authentication (MFA) and how does it work?
Multi-factor authentication (MFA) is an authentication method that requires users to provide two or more verification factors to gain access to a system, application, or account. It works by combining something you know (like a password), something you have (like a smartphone authentication app), and something you are (like a fingerprint). This layered approach enhances security by ensuring that even if one factor is compromised, unauthorized access is still prevented.
What are the benefits of multi-factor authentication?
The benefits of multi-factor authentication include increased security, reduced risk of data breaches, and enhanced user trust. By implementing MFA, organizations can significantly improve their cybersecurity posture and protect sensitive information from unauthorized access, making it a critical component of modern security practices.
How does MFA enhance security compared to single-factor authentication?
MFA enhances security compared to single-factor authentication by requiring multiple forms of verification. While single-factor authentication relies solely on a password, MFA requires additional factors, which makes it much harder for attackers to gain access and reinforces the importance of strong authentication. Even if one factor, like a password, is compromised, the additional authentication factors provide a safeguard against unauthorized access.
What are some examples of multi-factor authentication methods?
Examples of multi-factor authentication methods include SMS codes, email verification, and authentication apps like Google Authenticator. Other methods can involve biometric scans, such as fingerprints or facial recognition, and hardware tokens. These diverse MFA methods provide flexibility and enhance security across various platforms and applications.
How can organizations implement multi-factor authentication effectively?
Organizations can implement multi-factor authentication effectively by first assessing their current security posture and identifying sensitive systems that require additional security measures, ensuring that multi-factor authentication works effectively. They should then choose appropriate MFA methods that align with their security needs, ensure adequate training for users, and regularly review and update their authentication systems to adapt to emerging threats.
What is adaptive multi-factor authentication and how does it work?
Adaptive multi-factor authentication is an advanced approach that adjusts the required authentication factors based on the context of the login attempt. Factors such as the user’s location, device, and behavior are assessed to determine the level of risk. If a login attempt is deemed high-risk, additional authentication factors may be required, thus enhancing security without burdening users during low-risk situations.
How does MFA help protect against cyber threats?
MFA helps protect against cyber threats by adding layers of security that make it significantly harder for attackers to gain unauthorized access. By requiring multiple factors for authentication, MFA can prevent unauthorized access even if a password is compromised, thereby mitigating potential data breaches and enhancing the overall security of an organization.
Why is it important to use MFA in today’s security landscape?
Using MFA in today’s security landscape is important due to the increasing sophistication of cyberattacks. With the rise of phishing attacks and credential theft, relying solely on passwords is no longer sufficient. MFA provides an additional security layer, ensuring that sensitive information is better protected and that organizations can maintain their security posture against evolving threats.