What Is a Security Operations Center (SOC)?
What is a Security Operations Center (soc): What It Is and How It Works
In today’s digital landscape, the Security Operations Center (SOC) stands as a crucial component for any organization striving to maintain a robust security posture. This article delves into the intricacies of a SOC, exploring its definition, importance, and key functions. We aim to provide a comprehensive understanding of how a SOC operates and why It is essential for safeguarding your organization against ever-evolving cyberthreats, and an effective SOC plays a crucial role in this process..
Understanding the Security Operations Center
The Security Operations Center, often referred to as SOC, is a centralized unit within an organization responsible for monitoring, detecting, analyzing, and responding to security incidents. The SOC team comprises security analysts, security engineers, and SOC managers who work collaboratively to protect the organization’s information assets. It serves as the central hub for all information security operations, including security strategy implementation., ensuring that security measures are in place and effectively functioning to mitigate potential security breaches. The SOC is the cornerstone of an organization’s defense against cyberthreats.
Definition of SOC
At its core, a SOC is defined as a dedicated facility or team that proactively monitors and analyzes an organization’s security posture on an around-the-clock basis. The primary function of a security operations center is to detect, analyze, respond to, and prevent cyberthreats. A SOC serves as the central command center for information security operations, employing a range of security tools and technologies to continuously monitor networks, systems, and applications. This proactive approach allows the security team to identify and address potential security events before they escalate into significant security incidents.
Importance of a Security Operations Center
The importance of a security operations center cannot be overstated in today’s threat landscape. With cyberthreats becoming increasingly sophisticated, organizations need a dedicated team focused on proactive security. A SOC helps improve your organization’s security posture by providing key capabilities, including:
- Continuous security monitoring
- Enabling rapid response to security incidents
- Ensuring compliance with security policies and procedures
By proactively addressing security threats, a SOC minimizes the impact of potential security breaches and protects the organization’s reputation and financial assets. Furthermore, a SOC can help manage the organization’s security architecture, ensuring that all security solutions are effectively integrated and functioning optimally.
Key Functions of a SOC
The key functions of a security operations center are multifaceted and crucial for maintaining a strong security posture. These functions are diverse and can include:
- Continuous security monitoring.
- Security incident detection and response.
- Threat intelligence gathering and analysis.
- Vulnerability management is a vital component of the SOC’s responsibilities in maintaining network operations.
- Compliance management.
SOC analysts play a vital role in analyzing security event logs, identifying suspicious activity, and escalating security incidents to the appropriate teams. The SOC team also collaborates with security engineers to implement and maintain security tools and technologies, ensuring that the organization’s security architecture is up-to-date and effective. Furthermore, a SOC develops and enforces security policies to govern security practices.
Components of a SOC Team
Roles of Security Professionals in a SOC
Within the security operations center, various security professionals assume specialized roles critical to its effective functioning. The chief information security officer (CISO) provides overall strategic direction for the managed SOC. information security. Security analysts in the information security operations center utilize various tools used to enhance their effectiveness. form the front line, continuously monitoring for security events and security incidents, analyzing potential cyberthreats, and escalating issues as needed. Effective collaboration among these roles is vital for an organization’s robust security posture. Our Security services are crucial for maintaining robust data security and protecting against potential threats. will guarantee proactive security.
| Role | Responsibilities |
|---|---|
| SOC Managers | Oversee the daily operations of the SOC, ensuring efficient workflow and resource allocation. |
| Security Engineers | Responsible for implementing and maintaining security tools and technologies, as well as designing and managing the organization’s security architecture. |
Structure of a SOC Team
The structure of a SOC team The security measures can vary depending on the size and complexity of the network operations. organization’s security needs. A typical SOC team includes Tier 1, Tier 2, and Tier 3 analysts. Tier 1 analysts They are the first responders, responsible for monitoring alerts and triaging potential threats within the information security operations center. security incidents. Tier 2 analysts conduct in-depth investigations of escalated security events, utilizing advanced security tools and techniques. Tier 3 analysts, often the most experienced members of the security team, focus on threat hunting, advanced incident response, and developing new security systems. security solutions. A well-defined hierarchy ensures efficient incident handling and knowledge sharing within the managed SOC, strengthening the organization’s security posture.. We assure your Infrastructure is Safe.
Training and Skills Needed
To be effective, a SOC analyst needs a broad range of skills and training. Essential technical skills include a deep understanding of networking, operating systems, and security tools used in both in-house SOC and outsourced SOC environments. like security information and event management (SIEM) systems and intrusion detection/prevention systems. SOC personnel must also possess strong analytical and problem-solving abilities to investigate security events and identify cyberthreats. Soft skills, such as communication and teamwork, are equally important for effective collaboration within the SOC team. Ongoing training and certifications in areas such as incident response, threat intelligence, and digital forensics are crucial for keeping SOC analysts up-to-date with the latest security data is crucial for effective threat detection. security threats and techniques. With the right security measures you will be secure around the clock.
Challenges Faced by SOCs
Common SOC Challenges
SOC challenges are multifaceted, stemming from factors like the ever-evolving cyberthreat landscape and the increasing complexity of information security. Many security operations centers struggle with alert fatigue due to the high volume of security events they must process daily. Talent shortages and the need for specialized skills also pose significant hurdles. Effectively managing the organization’s security infrastructure, including various security systems and tools. security tools and technologies, is another challenge. Addressing these common issues is essential for optimizing the security posture and ensuring the SOC can effectively respond to cyberthreats. We offer cutting-edge security solutions.
Addressing SOC Needs
To effectively address The SOC needs to be equipped with advanced tools used for monitoring and responding to incidents., organizations must invest in comprehensive SOC solutions and strategies. A well-defined security roadmap is crucial for aligning security measures with business objectives. Implementing security information and event management (SIEM) systems and automated incident response processes can help streamline security event analysis and reduce alert fatigue. Investing in continuous training and development for security analysts is essential to ensure the SOC team An effective SOC possesses the skills needed to combat emerging threats and protect organizational assets. cyberthreats. By taking these steps, organizations can significantly improve their organization’s security posture by leveraging a dedicated SOC. and enhance the effectiveness of the security operations center.
Overcoming Operational Hurdles
Overcoming operational hurdles within a SOC requires a strategic approach to optimizing processes and resource allocation. Organizations should focus on automating routine tasks to free up analyst time for more complex investigations. Improving collaboration between the SOC team and other IT departments can enhance incident response capabilities through a dedicated SOC. Establishing clear security policies and procedures is essential for guiding security operations Automating processes is key to ensuring consistency and efficiency in data security practices. Regularly assessing and refining the SOC’s performance metrics can help identify areas for improvement. We assure your Infrastructure is Secure, Safe, and able to tackle operational challenges and maintain normal operations during incidents.
Tools and Technologies in SOC Operations
Essential Tools for a SOC
A modern security operations center relies on a suite of security tools and technologies to effectively monitor and respond to cyberthreats. Security information and event management (SIEM) systems are critical for collecting, analyzing, and correlating security event data from various sources. Intrusion detection and prevention systems (IDPS) help identify and block malicious activity on the network. Security professionals utilize vulnerability scanners to identify weaknesses in systems and applications. Endpoint detection and response (EDR) solutions provide advanced threat detection and incident response capabilities on individual endpoints. TeamWin offers enterprise AI-driven next-generation firewalls and real-time Dark Web monitoring.
Technologies Enhancing SOC Efficiency
Several technologies are emerging to enhance the efficiency and effectiveness of the security operations center. Artificial intelligence (AI) and machine learning (ML) can automate threat detection, reduce false positives, and improve incident response times. Threat intelligence platforms (TIPs) provide valuable insights into emerging cyberthreats and attacker tactics, techniques, and procedures (TTPs). Automation and SOC tools can streamline security operations. orchestration tools can streamline incident response workflows, enabling security analysts to respond to security incidents more quickly and effectively. By leveraging these technologies, organizations can optimize their security operations and proactively manage the organization’s security architecture.
Integrating New Tools into SOC Workflow
Integrating new security tools into the SOC workflow requires careful planning and execution, especially when involving security experts. It is essential to define clear objectives for the new tool and how it will improve the SOC’s capabilities. Conduct thorough testing to ensure the tool integrates seamlessly with existing systems and processes. Provide comprehensive training to the SOC team to ensure they can effectively utilize the new tool. Establish clear metrics to measure the tool’s performance and effectiveness. Regularly review and refine the integration process to optimize its impact on security operations. If you want to improve your organization’s security posture we are here around the clock.
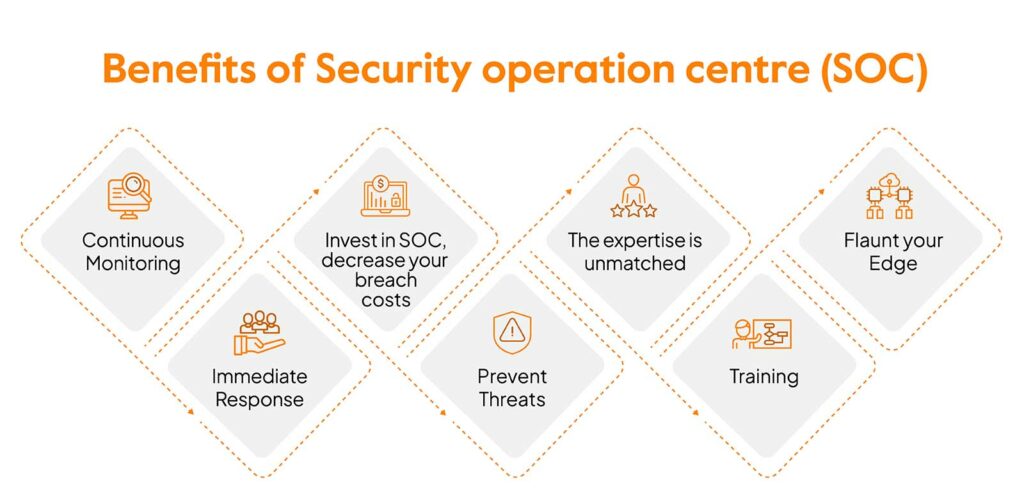
Benefits of a Security Operations Center
Improved Cyber Threat Detection
One of the most significant benefits of a network operations center is its ability to respond to cyber threats effectively. security operations center is its ability to provide improved cyberthreat detection. Our SOC employs advanced security tools and technologies, such as security information and event management systems, intrusion detection systems, and threat intelligence platforms, to continuously monitor the organization’s security environment. Our security team can quickly identify and analyze suspicious activity, leveraging real-time data and analytics to detect and respond to cyberthreats before they cause significant damage. TeamWin offers enterprise CCTV and biometric systems, firewalls, robust endpoint security, privileged access management, endpoint protection management, and networking capabilities.
Streamlined Incident Response
A well-functioning security operations center streamlines incident response, enabling the security team to quickly and effectively respond to security incidents. By centralizing security monitoring and analysis, the SOC team can rapidly assess the scope and impact of a security incident and coordinate response efforts with the help of security experts. Security analysts follow established incident response plans and procedures, ensuring a consistent and efficient approach to incident containment, eradication, and recovery. This streamlined approach minimizes downtime and reduces the potential for data loss, protecting the organization’s security posture. TeamWin offers around-the-clock support and proactive security, ensuring immediate assistance and reliable security solutions whenever needed.
Enhanced Security Posture
Ultimately, a security operations center enhances the organization’s security posture by providing continuous security monitoring, proactive threat detection, and rapid incident response capabilities. By implementing robust security orchestration, organizations can enhance their security systems. security policies and procedures, the SOC helps to enforce security measures across the organization. The SOC team actively manages vulnerabilities, ensuring that systems and applications are patched and hardened against potential attacks. Through these efforts, the security strategy is significantly improved. security operations center minimizes the risk of security breaches and helps to protect the organization’s critical assets. TeamWin offers managed security service provider and security policies ensuring you have the best information security possible. Our security services guarantees proactive security.
Optimizing SOC Performance
Strategies for Optimization
To optimize SOC performance, organizations should focus on several key strategies. Automating routine tasks, such as alert triage and incident investigation, can free up analyst time for more complex cyberthreat analysis. Implementing threat intelligence platforms can provide valuable insights into emerging security threats, enabling security analysts to proactively identify and mitigate risks. Regular training and development for the security team are essential to ensure they possess the skills needed to combat evolving cyberthreats. Regularly refining security policies and procedures is essential for guiding security operations and ensuring consistency. We offer cutting-edge security solutions.
Measuring SOC Effectiveness
Measuring SOC effectiveness is crucial for understanding its value and identifying areas for improvement. Key performance indicators (KPIs) can be used to track the SOC’s performance in areas such as incident detection rates, incident response times, and the number of vulnerabilities remediated. Regularly assessing the SOC’s ability to meet security objectives is essential. Gathering feedback from stakeholders, such as IT departments and business units, can provide valuable insights into the SOC’s effectiveness. By monitoring these metrics, organizations can ensure that the SOC uses the best practices for effective data security. security operations center is delivering value and effectively protecting the organization’s security posture. TeamWin offers enterprise AI-driven next-generation firewalls and real-time Dark Web security monitoring.
Future Trends in SOC Operations
The future of SOC operations is likely to be shaped by several key trends. Artificial intelligence (AI) and machine learning (ML) will play an increasingly important role in automating threat detection and incident response. Cloud-based SOC solutions will become more prevalent, offering scalability and cost-effectiveness. Threat intelligence sharing will become more collaborative, with organizations sharing information about emerging cyberthreats. The lines between physical and cybersecurity will continue to blur, requiring security operations centers to address both types of security threats. To be proactive with security means to know these security threats exist.
5 Surprising Facts About Security Operations Centers (SOCs)
- SOCs can operate 24/7, providing round-the-clock monitoring and response to security incidents.
- Many SOCs use advanced artificial intelligence to enhance their threat detection capabilities.
- The concept of SOCs originated in the early 2000s, evolving from traditional network security practices.
- Some organizations choose to outsource their SOC operations to Managed Security Service Providers (MSSPs) for cost efficiency.
- SOCs not only focus on cybersecurity threats but also play a role in compliance and regulatory requirements for organizations.
What is a Security Operations Center (SOC)?
A Security Operations Center (SOC) is a centralized function within an organization that is responsible for monitoring, detecting, and responding to security incidents in real-time. It acts as the hub for cybersecurity technologies and operations, employing a team of IT security professionals who work together to protect the organization’s information systems and data.
What are the Key Functions of a SOC?
The key SOC functions include continuous monitoring of security alerts, incident response, threat intelligence analysis, and maintaining compliance with industry standards like the Payment Card Industry Data Security Standard (PCI DSS). The SOC is also responsible for optimizing a security posture while preventing potential security breaches.
What are the Benefits of a SOC?
The benefits of a SOC include improved incident detection and response times, enhanced overall security posture, and the ability to manage security incidents more effectively. By utilizing expert security analysts and the latest security solutions, organizations can mitigate security threats before they escalate into serious issues.
How Does a SOC Help Organizations?
A SOC helps organizations by providing a structured approach to cybersecurity. It allows the SOC to monitor traffic based on security rules, identify threats, and respond to security threats swiftly. This proactive stance is essential in minimizing the impact of security incidents on business operations.
What is SOC as a Service?
SOC as a Service refers to the outsourcing of security operations to a third-party provider. This model allows organizations to leverage a team of IT security professionals without the need for in-house resources. Outsourced security operations can provide access to advanced technologies and expertise, ensuring that organizations maintain a robust security posture.
What Challenges Does a SOC Team Face?
The challenges faced by a SOC team include the ever-evolving threat landscape, the need to constantly update cybersecurity technologies and operations, and the pressure to respond quickly to security incidents. Additionally, a SOC must cope with staffing challenges and the requirement to maintain SOC maturity through continuous improvement and training.
How Can Organizations Optimize their Security Posture with a SOC?
Organizations can optimize their security posture by implementing a well-defined security road map, investing in next-generation SOC capabilities, and ensuring continuous training for their security engineers. Additionally, leveraging a managed security service can enhance the effectiveness of the security operations team in detecting and responding to threats.
What is the Role of Experienced Security Analysts in a SOC?
Experienced security analysts play a crucial role in a SOC by analyzing security incidents, conducting threat assessments, and developing response strategies. Their expertise allows the SOC to stay ahead of potential threats and improve overall security operations through informed decision-making.
How Does a SOC Manage Security Incidents?
A SOC manages security incidents through a structured incident response process. This involves identifying and classifying security incidents, analyzing their impact, and coordinating an appropriate response. The SOC will work to restore normal operations while ensuring that lessons learned are documented to improve future responses.

![What is Security Operations Center (SOC)? | [A Quick Overview]](https://sprinto.com/wp-content/uploads/2023/01/Blog_131_What_is_SOC_A_Quick_Overview-03.jpg)