All
IT Security
Network Security
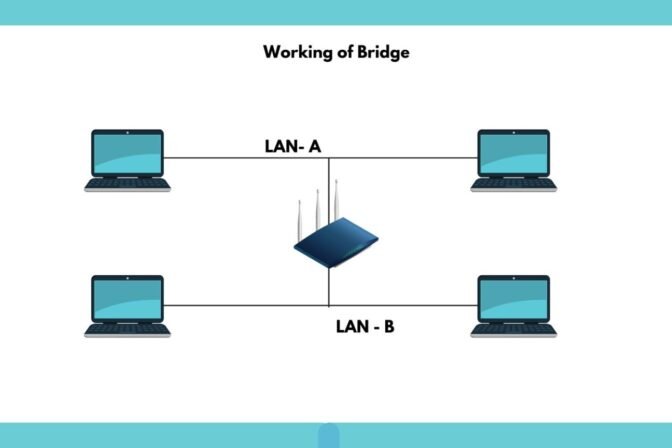
Networking
WiFi
Cybersecurity
Cloud Security
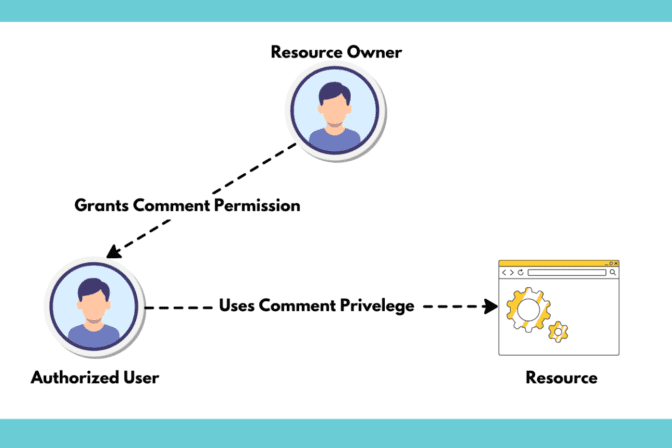
Security
Artifical Intelligence
Endpoint Security
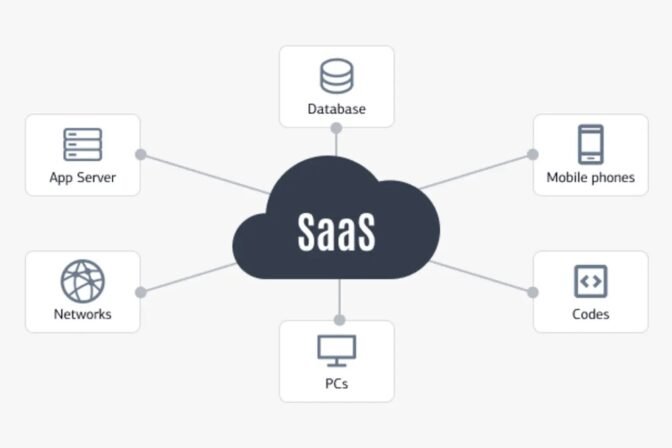
SaaS Security
IT Services
Cloud Solution
IT-Solutions
Tech Articles News
IT Management
Digital Networking
All
- By Teamwin
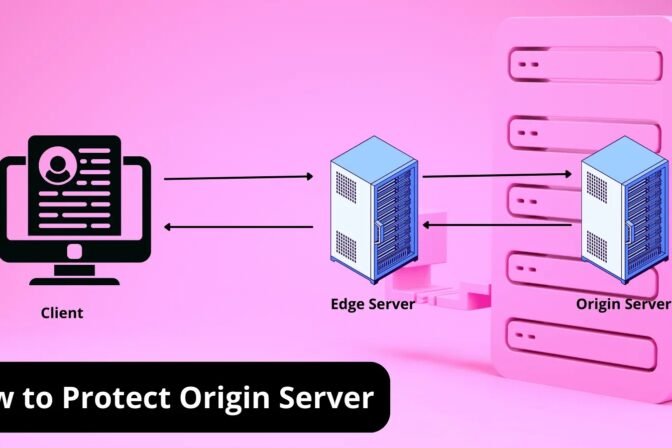
- Cybersecurity, Network Security
- Comments off
- 10
- By Teamwin
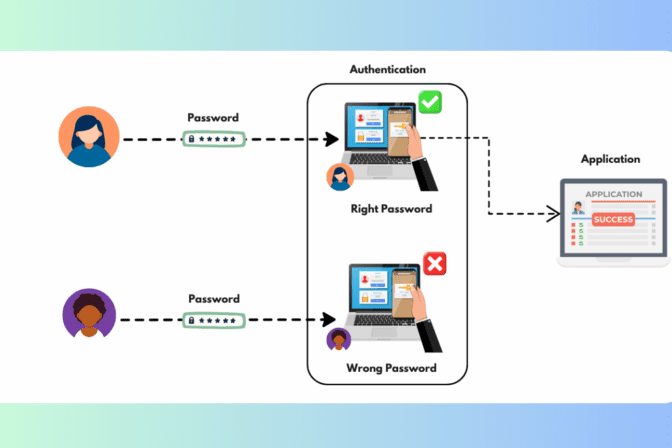
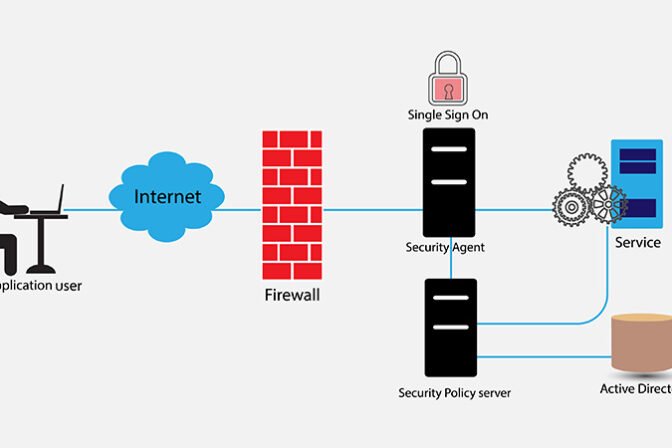
- IT Security
- Comments off
- 11
- By Teamwin
- Networking
- Comments off
- 14
- By Teamwin
- Cybersecurity, Networking
- Comments off
- 10
- By Teamwin
- Cybersecurity, WiFi
- Comments off
- 7
- By Teamwin
- IT-Solutions
- Comments off
- 12
- By Mohan Kumar Siramdasu
- Security
- Comments off
- 11